New Year CTF 2025
复现一下西电平台的题目
See you again
1 | from random import* |
这里拿到题目先观察加密方式
这里我们发现是矩阵RSA,这里是将明文分为四段放入矩阵当中
这里先贴个论文
要想知道具体的加密过程就要先了解什么是一般线性群
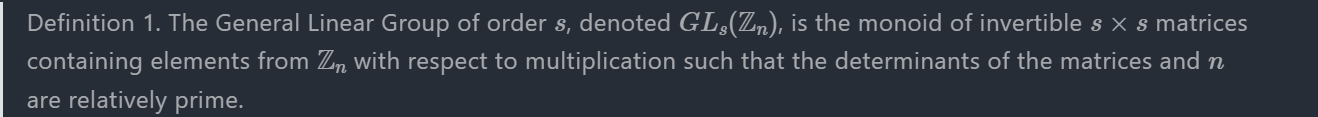
单位矩阵 I 属于 GLs(ℤn),矩阵乘法满足结合律,矩阵行列式与 n 互质即 GLs(ℤn) 中每一个元素都有乘法逆元,所以构成一个群。
那么要想解密也很容易
只要求出d Cd = m mod (n) 那么这里d要怎么求
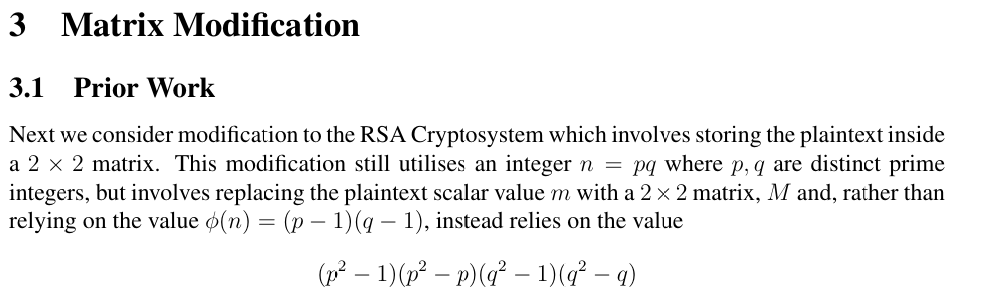
论文中给出了明确的求法,我们phi不再是之前了而是(p2 − 1)(p2 − p)(q2 − 1)(q2 − q)
那么现在我们要求的是p,q了
但是对于这题来说有个小小的非预期,phi好像怎么取值都行,原本我的理解是M的阶刚好是(p − 1)(q − 1)
但是,这里真的好像取啥都行,问了其他师傅,说是数据给的有问题
回到题目我们要怎么求p,q呢
1 | x1=randint(0,2**11) |
这里还是很简单的
我们会发现x1,x2都不是很大,那么可以选择爆破
将第一式乘x2,第二式乘x1
$$ hint1*x_{2}=x_{2}*(x_{1}*p+y_{1}*q) \\ hint2*x_{1}=x_{1}*(x_{2}*p+y_{2}*q) $$
现在再将两式相减
hint1 * x2 − hint2 * x1 = (x1y2 − x2y1)q
即
A = Bq
那么接下来只要做个gcd就可以得到q了
1 | n = 73072541902206871020737492238712393160727227031674788366854370087046494314953414149210811810993251599137993812618059430654795580640655927531189983107761278404614174799313759634478308102715209502959314132742690028687179640727016334879648957747421327650216141691465903844138851357328611067635106605344718049129 |
加下来就是恢复M了,上面也说过了
1 | import gmpy2 |
hnnnnnp
1 | from Crypto.Util.number import * |
第一眼以为是简单的hnp,但是仔细观察后发现并没有那么简单,题目中泄露的是高10位
那么肯定是要构造格的
具体的过程就不说了
鸡块师傅博客有讲过类似的,他说的肯定比我好
这里贴我自己的exp
1 | A = [99293334762228409415871581396212237412953404357126780770028017803413316507688, 2500480840704745075911410946123687629524432551367413638642986009358154787372, 80685558004752117053336613030689142016338319732790152841247856882805636400967, 63290001864400721248272352929255137611989584118097077958408567982128698234534, 5048332633026992532834890641901394670789207101467603380531070147563959907435, 98345158033169941273559370561319923206165641360286918926165722533747367869044, 91661185592644662634101002232848898241014068680383461946834577089141708799408, 35883539106260317692857231527467938791115349400928738495153295603754797497003, 18850448551910645282253407416422777216080885714433351260880371928669115264186, 86803241348387239192288300857910031249784969059106976374312551858268245857442, 113779438160927993654998705272524709206271659504623230967447802327094495796781, 13735459600754846538171144203957927429136626155419829429669861649940998894997, 46280418602037825886010980190704083111219707606955301840430515744873877438775, 16278994219375932354158092674595809845774952941618307320565305777822420450943, 74927876286842101149511766920644259934347532918716712290257161737641674460298, 42178202650652528099749516560693500619443362792978884623518490495115906200316, 19151047172626938357474963053807928227857518257319920099967861099963796480418, 21787599078683620242310742514553440060243832982887133694157543001440264793591, 34075119848054572416068714633191349442086346533132115388443988285733183568037, 70884300905035090978863770641828348559532542870751550058652309789615992321329, 56638844602601914284538086316463617187093124581243824454129547501609966433533, 63173126643011517652232352750442686295089111186360350917063529989062125715462, 28513769949842169592533398466043837164454663770876296609570694346056935679972, 78576986164864622274471458294234572339552498559596959190642129314202635344362, 29040128818027182812085632623851615750950738459702000094747611239508626643986, 24643036623783907525543153714744708140593035044888678308137488533907283671880, 114371475713932020306500291701047080632524480018017816508069308216548075509192, 41900448697162816841352108181063898351906757401259309332438722605718438845658, 54568329635023979120173438773482273886435623791438511491045655663987235054396, 75001704264552278370093948911424867598236273326722937206696873331699786435512, 26706895892299062149149150389452432539968783870299486337639175716389699841556, 97377367425189290583063973155451138814295009389822857196761177411699410905996, 1232863831096632130472661739812011549745300164338793700648153670333514662537, 26269418325008581770232430581427109657764847410045079633943766642502404580438, 24030674773281787758235075763804799489668709537838088140878504368601473605962, 86811629367335760989061373668208214074416802123960391077272719421979492321722, 4705372930912236219640794828821928446476233836995906942068634486045889421427, 3780622760283474933545118612904995151472952554666209520142018462683489410492, 32331832055598312449459015904562983681658454867302312991024083766727098901481, 82703349291431759834259791616748332088687686947094717519824850606996211446209] |
Before Sunset
1 | from Crypto.Util.number import * |
没什么好说的两次加密,和SHCTF有相同的
那么很自然想到利用mitm攻击来打
1 | import itertools |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 yskm!
